Please Install And Activate Gtranslate Plugin
About us
It takes more than a private internet browser to go incognito. We’ll make your real IP address.
Your IP Address:
- 216.73.216.96, 104.23.197.4
Your Location:
- ,
Your Status:
Unprotected
It takes more than a private internet browser to go incognito. We’ll make your real IP address.
Unprotected
CoverMeVPN has got everything you need to keep your data safe and have a great time online. They offer fast connections, global server access, military-grade encryption, and a strict no-logs policy. Whether you’re using it for work or just for yourself, CoverMeVPN has your back. It’s all about giving you the freedom to explore the internet without any worries.

Covermevpn is trusted by over 1 million forward thinking customers worldwide.


Enjoy the fast speed and unlimited bandwidth. Browse, stream, and download now risk-free.
Read More



You can connect up to 5 devices simultaneously in one household to the VPN at once.
Read More

You get a no-logs policy, so no latency when streaming Netflix, playing games, or downloading torrents.
Read More

Use 256-bit military grade encryption to stay safe and secure your data.
Read More

Professionals are on hand 24 hours a day, 7 days a week, with instant email responses and live chat.
Read More



Connect to 3000+ active VPN servers with PPTP, L2TP, IKEV2, SSTP, TCP, or UDP VPN protocol.
Read MoreWe are the most Extanded VPN provider from the globe , able to provide our services at supreme turbo speed to over 140+ countries + 350 different locations , cities , areas.. with over 3000 Servers and over 300.000 shared IPs , at short time renewed . Our network allows us to guarantee 99.9% up time with 100% satisfaction guarantee to or subscribers.
We offers up to 5 simultaneous logins , so you can protect your desktop PC, tablet, smartphone, laptop, and Mac with a single account. And unlimited devices protected if you setup your Wi-fi Router with our service (thats mean any device wich will be connected to your routr will be protecte). for more info read tutorials.
You can choose to subscribe to our VPN services for a IP dedicated which means that only you will have access to connect from that IP , and that IP will be static you will be able to keep the same IP as much as your subscription will not expire and you will not renew. This dedicated IPs are available just from 6 countries: US, UK, Canada, Germany, Australia, Singapore.
Private IP numbers are unique addresses provided to devices connected to a local network, therefore guaranteeing safe communication free from public internet access. These IPs (such as 10.x.x.x or 192.168.x.x) improve security, help to control network traffic, and lower IP conflicts.
CovermeVPN lets customers search safely, guard private information, and keep anonymity by supplying private IP numbers. CovermeVPN lets you keep your network safe from cyberattacks and enjoy a steady and encrypted connection.
Shared IPs is available from over 140+ countries and 350 different locations over 300.000 IPs etc. Dynamic IP means that you will not be able to keep same IP for long time. Our Dynamic IPs will automatically renewed at a period of time , regularly few days.
CoverMeVPN offers a solution with Shared IPs for extra privacy, secure encryption to protect sensitive data, and a fast, reliable network. With CoverMeVPN, you can bypass geo-restrictions and access content freely, while ensuring complete online anonymity and protection from cyber threats. Stay safe and secure with CoverMeVPN’s private IP numbers, the best way to enhance your online privacy.

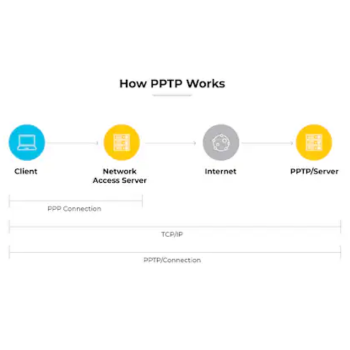
Stands for “Point-to-Point Tunneling Protocol.” PPTP is a networking standard for connecting to virtual private networks, or VPNs. VPNs are secure networks that can be accessed over the Internet, allowing users to access a network from a remote location. This is useful for people who need to connect to an office network from home or access their home computer from another location.
The “point-to-point” part of the term refers the connection created by PPTP. It allows one point (the user’s computer) to access another specific point (a remote network) over the Internet. The “tunneling” part of the term refers to the way one protocol is encapsulated within another protocol.
In PPTP, the point-to-point protocol (PPP) is wrapped inside the TCP/IP protocol, which provides the Internet connection. Therefore, even though the connection is created over the Internet, the PPTP connection mimics a direct link between the two locations, allowing for a secure connection.
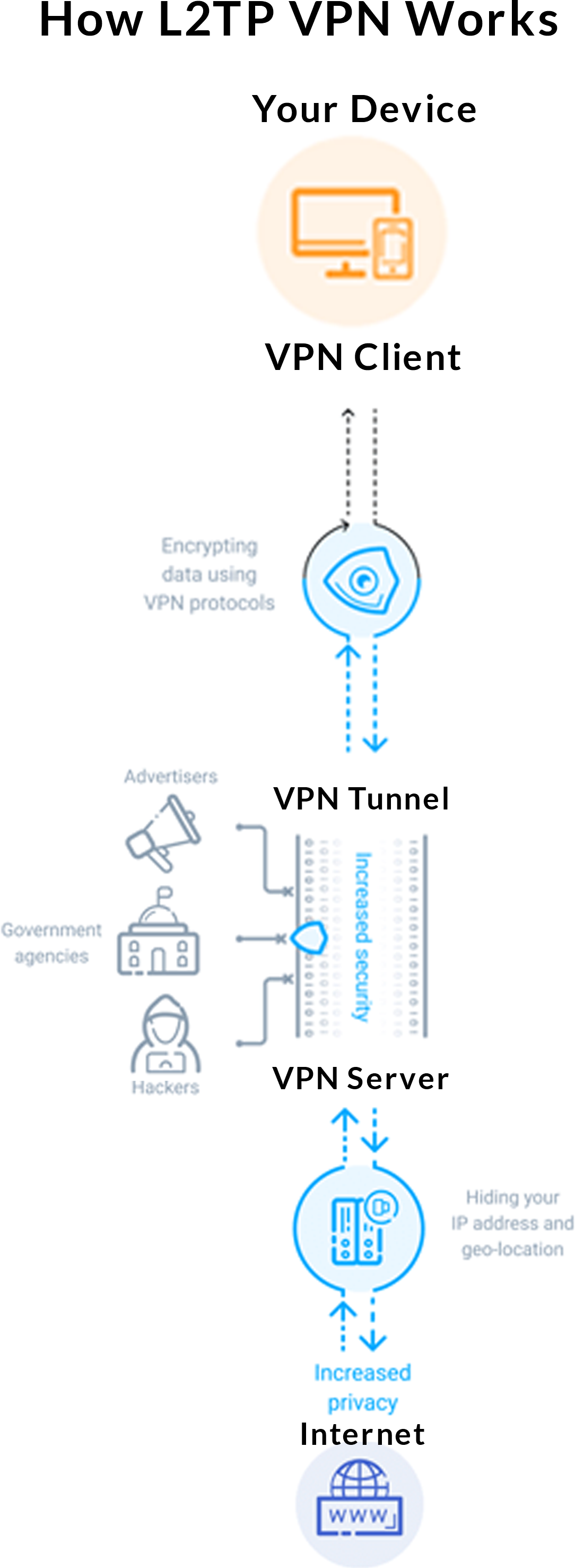
Layer Two Tunneling Protocol (L2TP) is an extension of the Point-to-Point Tunneling Protocol (PPTP) used by an Internet service provider (ISP) to enable the operation of a virtual private network (VPN) over the Internet. L2TP merges the best features of two other tunneling protocols: PPTP from Microsoft and L2F from Cisco Systems.
The two main components that make up L2TP are the L2TP Access Concentrator (LAC), which is the device that physically terminates a call and the L2TP Network Server (LNS) which is the device that terminates and possibly authenticates the PPP stream.PPP defines a means of encapsulation to transmit multiprotocol packets over layer two (L2) point-to-point links. Generally, a user connects to a network access server (NAS) through ISDN, ADSL, dialup POTS or other service and runs PPP over that connection.
In this configuration, the L2 and PPP session endpoints are both on the same NAS.L2TP uses packet-switched network connections to make it possible for the endpoints to be located on different machines. The user has an L2 connection to an access concentrator, which then tunnels individual PPP frames to the NAS, so that the packets can be processed separately from the location of the circuit termination. This means that the connection can terminate at a local circuit concentrator, eliminating possible long-distance charges, among other benefits. From the user’s point of view, there is no difference in the operation.
Like any VPN protocol, IKEv2 is responsible for establishing a secure tunnel between the VPN client and the VPN server. It does that by first authenticating both the client and the server, and then agreeing on which encryption methods will be used. We already mentioned that IKEv2 handles the SA attribute, but what is SA? Simply put, it’s the process of establishing security attributes between two network entities (in this case, the VPN client and the VPN server). It does that by generating the same symmetric encryption key for both entities. Said key is then used to encrypt and decrypt all the data that travels through the VPN tunnel.
IKEv2 supports IPSec’s latest encryption algorithms, alongside multiple other encryption ciphers.
Generally, the IKE daemon (a program that runs as a background process) runs in the user space (system memory dedicated to running applications) while the IPSec stack runs in kernel space (the core of the operating system). That helps boost performance.
The IKE protocol uses UDP packets and UDP port 500. Normally, four to six packets are necessary for creating the SA.
The IKEv2 VPN protocol supports MOBIKE (IKEv2 Mobility and Multihoming Protocol), a function that allows the protocol to resist network changes. IKEv2 supports PFS (Perfect Forward Secrecy). While IKEv2 was developed by Microsoft together with Cisco, there are open-source implementations of the protocol (like OpenIKEv2, Openswan, and strongSwan). IKE uses X.509 certificates when it handles the authentication process.
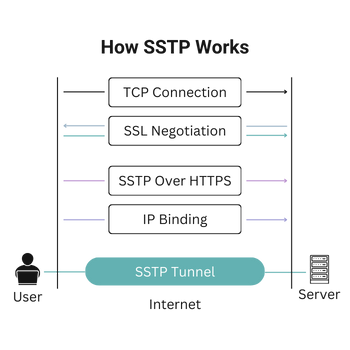
What is SSTP? Secure Socket Tunneling Protocol (SSTP) is a secure protocol used in VPN tunneling. The protocol, though owned by Microsoft, is available to both Linux and Mac users. SSTP uses SSL/TLS (Secure Socket Layer/Transport Layer Security) channel over TCP 443 port.
How Does SSTP Work? A client’s system connects to a server through a TCP (Transmission Control Port). SSL uses the 443 port to connect to the server. To confirm the connection, it requires user authentication. And, it is usually authenticated by the client. The protocol uses the server certificate for authentication.
Why is SSTP a Popular VPN Protocol?There are many reasons that endorse the popularity of SSTP. For instance, SSTP offers the highest level of security, i.e., 256-bit AES encryption. Moreover, the port it uses can circumvent almost all types of firewalls. Since it is a Microsoft owned property, it is completely compatible with Windows.
Transmission Control Protocol (TCP) – a connection-oriented communications protocol that facilitates the exchange of messages between computing devices in a network.
It is the most common protocol in networks that use the Internet Protocol (IP); together they are sometimes referred to as TCP/IP.
TCP takes messages from an application/server and divides them into packets, which can then be forwarded by the devices in the network – switches, routers, security gateways – to the destination. TCP numbers each packet and reassembles them prior to handing them off to the application/server recipient. Because it is connection-oriented, it ensures a connection is established and maintained until the exchange between the application/servers sending and receiving the message is complete.
For example, when an email (using the simple mail transfer protocol – SMTP) is sent from an email server, the TCP layer in that server will divide the message up into multiple packets, number them and then forward them to the IP layer for transport. At the IP layer, each packet will be transported to the destination email server.
While each packet is going to the same place, the route they take to get there may be different. When it arrives, the IP layer hands it back to the TCP layer, which reassembles the packets into the message and hands it to the email application, where it shows up in the Inbox.
User Datagram Protocol (UDP) – a communications protocol that facilitates the exchange of messages between computing devices in a network. It’s an alternative to the transmission control protocol (TCP). In a network that uses the Internet Protocol (IP), it is sometimes referred to as UDP/IP.
UDP divides messages into packets, called datagrams, which can then be forwarded by the devices in the network – switches, routers, security gateways – to the destination application/server. While UDP does not number or reassemble the datagrams, it does include port numbers in the datagram header that help distinguish different user requests and an optional checksum capability that can help verify the integrity of the data transferred.