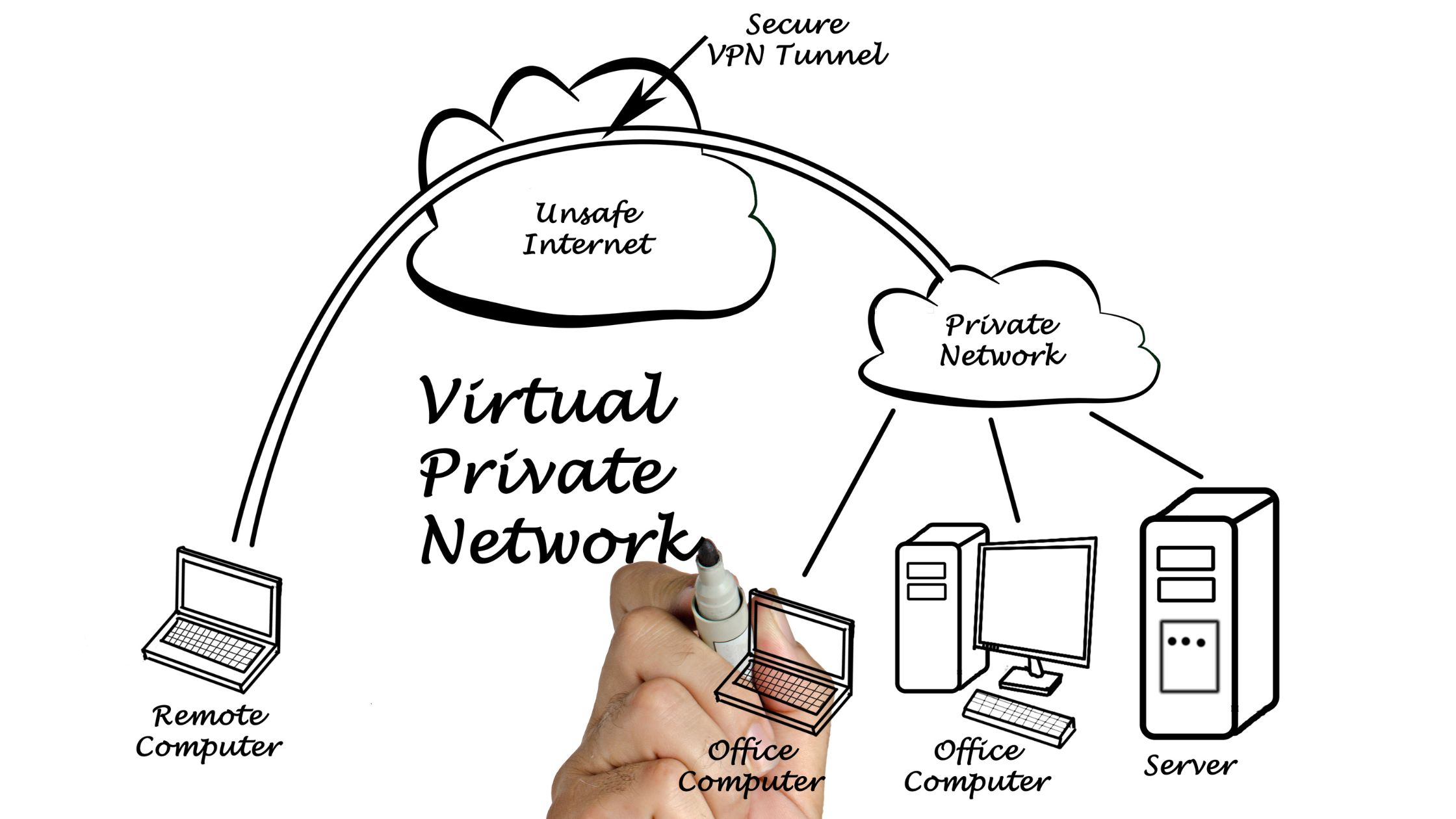
A Virtual Private Network (VPN) enhances online privacy and security by establishing an encrypted connection over a public or less secure network. By masking your IP address and routing your internet traffic through a remote server, VPNs make it significantly harder for third parties, including ISPs, advertisers, and potential cybercriminals, to track your online activities. This not only protects your browsing history and personal data but also allows you to bypass geo-restrictions and access content that might otherwise be unavailable. While even secure Wi-Fi connections can be vulnerable, a VPN adds a crucial layer of encryption, safeguarding your data from interception and ensuring greater anonymity.
Why do you need a VPN service?

Using public Wi-Fi? Your data’s at risk. A VPN creates a secure, encrypted tunnel for your internet traffic, hiding your IP address and protecting your online activity—emails, banking, browsing—from potential eavesdroppers. For anyone concerned about privacy and security, especially when using unsecured networks, a VPN is an essential tool. Experts recommend using a VPN to safeguard sensitive information and maintain online anonymity.
How a VPN protects your IP Address and Privacy
Think of a VPN like a secret tunnel for your internet. It hides your location and protects your information. When you use public Wi-Fi, anyone nearby might see what you’re doing online. A VPN scrambles your data, making it unreadable to them.
Here’s how it works: Your internet traffic goes through a VPN’s server, which can be anywhere in the world. This makes websites and apps think you’re in that location, letting you access things you normally couldn’t. Also, your internet company can usually see everything you do online. A VPN hides this, because your activity looks like it’s coming from the VPN server, not your home. While search engines themselves also collect information, your VPN stops them from directly linking that information back to you.
Experts agree: a VPN adds a crucial layer of privacy and security, especially when using public Wi-Fi. It’s a simple way to keep your online activities private and secure.
VPN privacy: What does a VPN hide?
A VPN can hide a lot of information that can put your privacy at risk. Here are five of them.
1. Your browsing history
Your online activity isn’t as private as you think. Your internet provider and web browser often track everything you do. Websites also collect your data, linking it to your IP address.
Why is this important? Imagine searching for medical information. Without a VPN, you might see targeted ads related to your condition, revealing private details. Or, when shopping for flights, travel sites might show you inflated prices, knowing you’re interested.
These are just a few examples. Your internet provider could even sell your browsing history. Even “private” browsing modes offer limited protection.
Experts in online privacy emphasize the need for tools like VPNs to protect sensitive information. Using a VPN prevents your IP address from being directly linked to your online activities, adding a vital layer of privacy and security.
2. Your IP address and location
Your IP address is like your online home address. Anyone who has it can see what you’ve been doing online and where you were. That’s why protecting it is crucial.
A VPN hides your real IP address and replaces it with another one. This makes your online searches anonymous and stops others from tracking, viewing, or selling your browsing history.
However, remember: if you use a public computer (like at a library) or a computer provided by your work or school, your activity might still be visible. Experts in cybersecurity recommend being aware of your environment and the potential for monitoring, even when using a VPN.
3. Your location for streaming
Sometimes, when you travel, your favorite streaming services might not work. This is often due to licensing agreements or local rules. For example, you might miss your favorite sports games.
A VPN can help. By letting you choose an IP address from your home country, it often tricks the streaming service into thinking you’re still there. This can give you access to the shows and events you pay for. Plus, some internet providers slow down your connection (called throttling), and a VPN can sometimes help you avoid that.
Experts in online streaming and VPN technology confirm this as a common use-case. Using a VPN to bypass geo-restrictions and maintain access to paid streaming services is a widely recognized and accepted practice.
4. Your devices
Your devices—phones, laptops, tablets—are vulnerable online, especially on public Wi-Fi. A VPN acts as a shield, protecting them from hackers.
It creates a secure, encrypted connection, meaning your data is scrambled. This prevents cybercriminals from seeing what you’re doing, whether you’re sending emails, browsing websites, or using apps.
Cybersecurity experts recommend using a VPN to enhance device protection, particularly when connected to unsecured networks. It’s a key step in safeguarding your personal information and online activity from potential threats.
5. Your web activity — to maintain internet freedom
While most people aren’t targets of government surveillance, it’s wise to protect your online privacy. A VPN hides your browsing history from your internet provider. This is important if a government agency requests your internet activity records from your provider.
It’s crucial to choose a VPN provider with a strict “no-logs” policy. This means they don’t keep track of your online activity. If your VPN doesn’t keep logs, it adds a layer of protection to your internet freedom.
Experts in digital privacy emphasize the importance of using a VPN with a reputable “no-logs” policy. This helps ensure that your browsing data remains private, even in cases where internet service providers are asked to share information.
How can a VPN help protect against identity theft?
Identity theft happens when someone steals your personal information to commit fraud in your name. A VPN can help protect you by creating a secure, encrypted tunnel for your data, making it harder for thieves to intercept.
Your smartphone, especially when connected to public Wi-Fi, is vulnerable. Everyday activities like online shopping and banking can expose your information. A VPN protects the data you send and receive, especially on public Wi-Fi, where hackers might try to steal your login details or credit card numbers.
While no one can completely prevent identity theft—data breaches happen—a VPN adds a crucial layer of security. Cybersecurity experts recommend using VPNs, particularly on mobile devices and when accessing public Wi-Fi, to significantly reduce the risk of your personal information being compromised.
What should you look for in VPN services?
Choosing a VPN can be tricky, as there are many options. To find the right one, think about what you need.
Ask yourself: Do you want to hide your location? Do you worry about security on public Wi-Fi? Do you travel and want to access your favorite shows?
A good VPN can do all of these things. But here are some key things to look for when making your decision. Experts in cybersecurity and digital privacy recommend considering these factors to ensure you choose a reliable and effective VPN that meets your specific needs.
How to choose a VPN
A smart way to stay secure when using public Wi-Fi is to use a VPN solution. But what’s the best way to choose a virtual private network? Here are some questions to ask when you’re choosing a VPN provider.
| Criteria | Description |
|---|
| Do they respect your privacy? | A VPN should have a strict no-log policy, ensuring that your online activities are never tracked or recorded. |
| Do they run the most current protocol? | OpenVPN offers stronger security than older protocols like PPTP. It is open-source and compatible with major operating systems. |
| Do they set data limits? | Check if the VPN provides full, unmetered bandwidth without data limits to match your internet usage needs. |
| Where are the servers located? | Ensure the VPN has servers in the locations you need to access the web from specific regions. |
| Will you be able to set up VPN access on multiple devices? | Ideally, the VPN should support simultaneous connections on multiple devices, as most users use 3-5 devices. |
| How much will it cost? | Free VPNs may seem attractive, but they often come with downsides like ads, data collection, or selling your information. Compare paid and free options carefully. |
- don’t offer the most current or secure protocols
- don’t offer the highest bandwidth and connection speeds to free users
- do have a higher disconnection rate
- don’t have as many servers in as many countries globally
- don’t offer support
There are many points to consider when you’re choosing a VPN, so do your homework to make sure you’re getting the right fit for your needs. Regardless of which provider you choose, rest assured that a good VPN will provide more security, privacy, and anonymity online than a public Wi-Fi hotspot can.
VPN glossary
Learning about VPNs may seem like it requires a specialized vocabulary. Here’s a glossary with definitions of some of the most common terms you’ll see.
AES encryption
Encryption is like a secret code for your online data. It scrambles information so that only someone with the right “key” can read it. This protects your data from hackers, companies, and even government snooping.
A very strong and widely used encryption method is called AES (Advanced Encryption Standard). Experts in cryptography, Joan Daemen and Vincent Rijmen, developed it. The U.S. government adopted AES as its standard in 2002, and it’s now used worldwide.
Essentially, AES is a highly trusted and robust way to keep your online information private and secure. It’s the gold standard for data protection.
Browser history
A record of all your internet activity using a particular web browser, including keywords you searched for and websites you accessed.
Geo-restrictions
Many people use VPNs to access content that’s blocked in their region. For example, streaming services like Netflix often have different shows and movies depending on where you are. This is called geo-restriction.
Using a VPN, you can choose an IP address from another country, like the UK, and potentially watch shows that aren’t available in your home country, such as the US. The VPN hides your real location.
However, it’s important to be aware of the streaming service’s terms of service. Some services may not allow this. Also, some countries have rules against using VPNs to bypass restrictions.
Experts in online streaming and VPN usage advise users to be aware of the legal and terms of service implications. While VPNs offer a way to bypass geo-restrictions, users should proceed with caution and respect the regulations of their streaming services and local laws.
Google search history

A record of all your internet searches using the Google search engine.
IP address
IP stands for Internet Protocol, and an IP address is a series of numbers and periods that identifies a computer that’s using the Internet Protocol to send and receive data over a network.
IPsec
IPsec is a set of rules that VPNs use to create a secure connection between your device (like a phone or laptop) and the internet. Think of it as the foundation for a secure VPN.
Without IPsec, VPNs couldn’t properly encrypt your data and protect your privacy. It’s the core technology that allows VPNs to keep your information safe. IPsec stands for Internet Protocol Security.
Experts in network security confirm that IPsec is a fundamental component of modern VPN technology. It is a widely recognized and trusted standard for ensuring secure and private online connections.
ISP
Short for Internet Service Provider, this is a service you pay for to connect to the Internet. ISPs can record your browsing history and may be able to sell it to third parties, for marketing or other purposes.
Kill switch
You use a VPN to keep your online activity private. But what if your VPN suddenly stops working? Your device would then use your regular internet connection, exposing your IP address and online activity.
A “kill switch” is a safety feature that solves this problem. If your VPN connection drops, the kill switch instantly cuts off your internet access. This ensures that your activity remains private, even if the VPN fails.
Not all VPNs have a kill switch. Experts in cybersecurity recommend prioritizing VPNs that include this feature. It’s a vital tool for maintaining consistent online privacy and security.
L2TP
L2TP is a set of rules that helps internet providers work with VPNs. Think of it as a way to create the “tunnel” for your VPN connection.
However, L2TP by itself doesn’t encrypt your data. This means it doesn’t fully protect your privacy. That’s why L2TP is almost always used together with IPsec, which does encrypt data, to create a secure and private connection.
Network security experts confirm that L2TP combined with IPsec is a common and reliable method for establishing secure VPN connections. While L2TP handles the tunneling, IPsec provides the crucial encryption layer.
Public Wi-Fi
A wireless network in a public place that allows you to connect a computer or other device to the internet. Public Wi-Fi is often unprotected and potentially accessible to hackers.
Search engines
A service that allows you to search for information using keywords on the internet. Many popular search engines record your search history and can make money off that information.
Service provider
A company that provides a virtual private network — essentially routing your connection through a remote server and encrypting the data.
Simultaneous connections
Most of us use many devices online, like phones, laptops, and computers. Good VPNs let you protect all of them at the same time with just one account.
This is really important. Even if you use a VPN on your laptop, your phone is still vulnerable without it. So, protecting all your devices ensures complete online privacy and security.
Experts in cybersecurity emphasize the importance of using a VPN on all your internet-connected devices. This ensures consistent protection against online threats and privacy breaches.
Virtual private network
A VPN creates a safe, private connection for you online, even when you’re using public Wi-Fi. It does this by hiding your IP address, which is like your online location.
Essentially, a VPN encrypts your internet traffic, meaning it scrambles your data. This makes it much harder for anyone to see what you’re doing online, protecting both your privacy and the security of the information you send and receive.
Cybersecurity experts recommend VPN usage to enhance online privacy and security. It is a tool that creates a secure and encrypted connection, therefore making your online activity more secure.
VPN connection
A virtual private network connection allows you to access the internet through a remote server, hiding your actual location and browser history, and encrypting your data.
VPN privacy
This refers to the privacy that using a VPN provides. For instance, a VPN encrypts your data, disguises your location, and conceals your browsing history and the data you transmit via the internet.
VPN clients
A VPN client is the software that lets you easily connect to a VPN. It’s the app you install on your phone, computer, or tablet.
Your devices often have basic VPN software built-in (like on Android, Windows, or iPhones). However, many people prefer using VPN apps from other companies. These often have more features or are easier to use.
Experts in VPN technology confirm that while built-in VPN clients exist, third-party clients often provide a superior user experience and more advanced features. Choosing a reputable third-party client can significantly enhance your VPN experience.
VPN protocols
Think of VPN protocols as the rules your VPN uses to create a secure connection. VPN providers use these rules to make sure you connect safely.
There are different sets of rules, each with pros and cons. OpenVPN is a very popular choice. It’s known for being secure and working on many devices. However, it can sometimes be a bit slower than other options.
Experts in network security confirm that OpenVPN is a widely trusted and secure protocol. While speed can vary, its robust security makes it a preferred choice for many users.
VPN provider
Synonymous with VPN service, this is a service you sign up for that allows you to connect to a virtual private network by providing a temporary IP address that hides your actual address.
VPN server
VPN services allow you to connect to the internet through remote servers that they either own or have access to. This disguises your location.
VPN service
A service you sign up for that allows you to connect to a virtual private network by providing a temporary IP address that hides your actual address.
VPN tunnel
You’ll often hear the term “VPN tunnel.” It’s simply the secure, encrypted connection your VPN creates between your device and the internet.
Whether you’re at home or using public Wi-Fi, a VPN tunnel hides your online activity. Your internet provider, companies, and even the government can’t see the websites you visit or the links you click. It also hides your real location by masking your IP address. Websites will only see the VPN provider’s location, not yours.
Cybersecurity experts often use the term “VPN tunnel” to describe this secure, encrypted connection. It is a vital component of online privacy and security, effectively shielding your online activity from unwanted observation.
VPN web browser
A web browser that includes a built-in VPN service, allowing you to hide your browsing activity on the internet.
Web search history
A record of what you searched for on the internet. Your internet service provider and your web browser likely have a complete history of your internet search activity.
Wi-Fi
A wireless network uses a radio frequency to connect your computer and other devices to the internet and each other.